| |
IETF workgroup as part of transport area workgroup.
|
| |
Formal work started April 1998 at IETF in Los Angeles with framework document
|
www.ietf.org/html.charters/diffserv-charter.html
Wed Mar 27 17:35:47 CST 2013
Untitled Document
|
Network Service Providers want to:
|
| | |
Offer a Scalable Service Differentiation (defined in SLA's) in stead of current best effort service.
|
| | |
Improve revenues through premium pricing and competitive differentiation.
|
|
Applications seek better than best effort:
|
| | |
Packet loss characteristics.
|
Wed Mar 27 17:35:47 CST 2013
Untitled Document
| |
DS is a relatively simple and coarse method to provide differentiated Classes of Service.
|
| |
Offers a small well defined set of building blocks from which several services may be built.
|
| |
Packet flows are classified (marked) at the network ingress and receive a certain forwarding treatment in the network.
|
| |
Multiple queuing mechanisms offer differentiated forwarding treatments.
|
Wed Mar 27 17:35:47 CST 2013
Untitled Document
| |
Create common understanding of forwarding treatment
|
| |
Agree on common packet marking semantics
|
| |
Establish commonly understood service categories
|
| |
experiment with forward treatments to identify additional services.
|
| |
Investigate additional components such as traffic shapers & packets markers needed at network boundaries.
|
| |
Define mechanisms such as LDAP schemata to map service profiles into Differentiated Services at the network boundary.
|
| |
Analyze security threats, such as theft of service.
|
Wed Mar 27 17:35:47 CST 2013
Untitled Document
| | |
Significant Characteristic of packet transmission in one direction across a set of one or more paths.
|
|
Characteristic Specification
|
| | |
In quantitative/statistical terms of throughput, delay, packet loss or jitter.
|
| | |
In terms of relative priority of access.
|
Wed Mar 27 17:35:47 CST 2013
Untitled Document
|
Service Provider Requirements
|
|---|
| | |
ISP requirements are driving force
|
| |
Permit differentiated pricing
|
| |
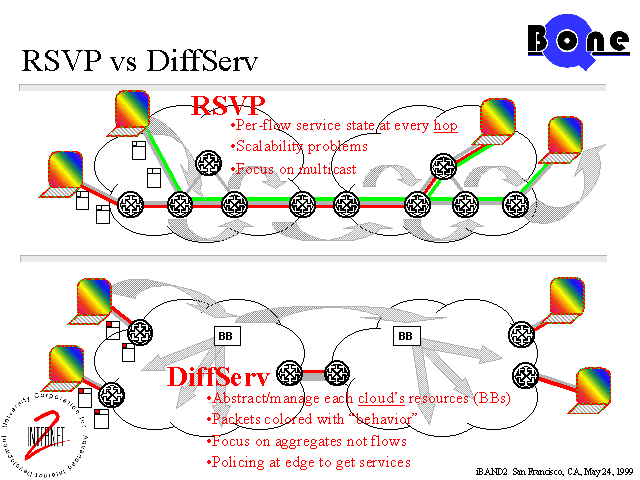
RSVP less attractive as it is perceived:
|
| | |
Too complex (read granular).
|
| | |
Not scalable to large aggregates: requires per flow state
|
| | |
As per Chicago IETF: MPLS seems strategic direction for binding RSVP flows to labels. (draft-ietf-mpls-rsvp-00.txt)
|
Wed Mar 27 17:35:47 CST 2013
Untitled Document
Wed Mar 27 17:35:47 CST 2013
Untitled Document
 Wed Mar 27 17:35:47 CST 2013
Untitled Document
Wed Mar 27 17:35:47 CST 2013
Untitled Document
| | |
Architecture implements per node:
|
| | |
Small set of queuing characteristics
|
| | |
Packet classification functions.
|
| | |
marking of packets through DS codepoints.
|
Wed Mar 27 17:35:47 CST 2013
Untitled Document
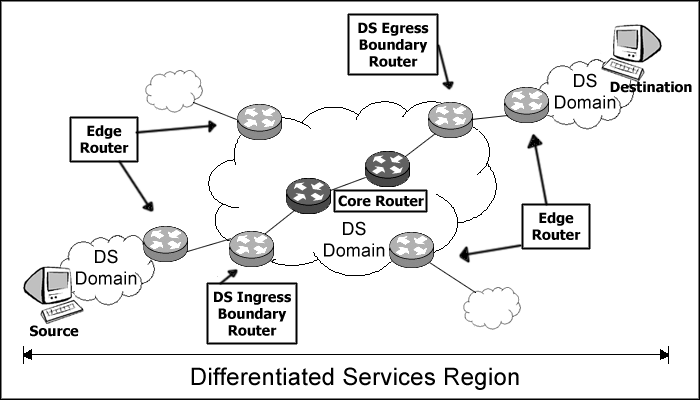
|
Classification and conditioning only at boundary nodes.
|
|
Apply PHB to aggregates of marked traffic in core of network.
|
|
PHB does not need to maintain a state per flow - core routers are flow-unaware.
|
|
Service provisioning and traffic conditioning can be separated from forwarding behavior.
|
|
Does not rely on hop by hop application signaling.
|
|
Compliant with existing non-DS network nodes.
|
Wed Mar 27 17:35:47 CST 2013
Untitled Document
|
Fixed SLA: (Statical Implementation)
|
| | |
fixed agreements which may identify periods of time during which a certain service level can be offered
|
|
Dynamic SLA (Dynamical Implementation)
|
| | |
Requires the provider network to adopt dynamic, automated resource provisioning mechanisms. (bandwidth brokers representing current network load)
|
| | |
Requires customer equipment to adapt to dynamic SLA¡¦s using some kind of signaling.
|
Wed Mar 27 17:35:47 CST 2013
Untitled Document
| | |
SLA¡¦s require the service provider to setup traffic conditioning components in order to protect the providers network:
|
| Meters
| measures conformance to a profile and provides input for below components implementing policing
| Markers
| police by demoting packets by remarking.
| Shapers
| add delay to packets such that its rate conforms.
| Droppers
| exceeding rate packets are dropped.
| | | |
|
Users must also be authenticated
|
| | |
(by physical connection or by cryptographic means)
|
Wed Mar 27 17:35:48 CST 2013
Untitled Document
| |
Traffic classifiers in boundary devices
|
| |
May separate traffic based on:
|
| | |
Based on multiple fields within the packet header and payload (MF classifier) offering certain per micro-flow services to non-DS clients.
|
| | |
Customer must mark & shape and provider polices (meters, drops and remarks)
|
| | |
Provider is able to classify/shape as an additional service
|
Wed Mar 27 17:35:48 CST 2013
Untitled Document
|
Expedited Forwarding (EF)
|
www.ietf.org/internet-drafts/drafts-ietf-diffserv-phb-ef-01.txt
www.ietf.org/internet-drafts/drafts-ietf-diffserv-af-03.txt
| |
Virtual Leased Line (Premium Service) based on EF
|
| |
Olympic Service (Gold, Silver and Bronze).
|
Wed Mar 27 17:35:48 CST 2013
Untitled Document
| |
Low loss, low latency, low jitter with assured bandwidth.
|
| |
Strict enforcement of traffic level.
|
| |
Strict queuing treatment.
|
| |
Strict administration of aggregate traffic levels to prevent queuing of EF traffic.
|
| | |
(Non-EF traffic will get queued and/or dropped).
|
| |
PHB can be implemented by more then one mechanism:
|
| | |
A queue with the highest priority with token bucket rate policer at ingress.
|
| | |
Single queue in a weighted round robin scheduler where weight is equal to bandwidth assigned.
|
| |
Looks like a virtual leased line
|
Paper Details
Wed Mar 27 17:35:48 CST 2013
Untitled Document
| |
4 classes with each 3 different levels of drop priority
|
| |
No re-ordering of packets if packets belong to same class.
|
| |
Each class can be allocated a certain amount of forwarding resources.
|
| |
Traffic conditioning MAY be done at the boundary.
|
| |
RED like discarding algorithm is RECOMMENDED and thresholds MUST be configurable.
|
| |
Exceeding traffic may be assigned a higher drop precedence
|
| |
Looks a bit like ABR with a certain minimum rate, peak rate and maximum burst size.
|
Wed Mar 27 17:35:48 CST 2013
Untitled Document
| | |
SSR implements DS components (in stages):
|
|
Traffic classification mechanisms:
|
| | |
Multi Field layer 2,3 and 4
|
WRED
|
Flow rate monitoring & policing thru token bucket algorithm (configurable 20ƒÝS-2S)
|
Wed Mar 27 17:35:48 CST 2013
Untitled Document
|
Understand application QoS requirements is number 1 problem:
|
| |
need for absolute per-flow assurances.
|
| |
adaptiveness of applications
|
| |
split single application into multiple flows with relative precedence
|
|
Investigate applicability of service types.
|
|
Investigate interoperability between DS aware domains
|
|
Investigate Security and Admission.
|
Wed Mar 27 17:35:48 CST 2013