Wireless Networks
Introduction to Wireless Networks
Principles and Fundamentals
First Generation Cellular Systems
Second Generation Cellular Systems
Third Generation Cellular Systems
Fixed Wireless Access Systems
Wireless ATM and Ad Hoc Routing
Personal Area Networks (PANs)
Economics of Wireless Networks
| Introduction to Wireless Networks |
|---|
Wireless Networks
by P. Nicopolitidis, M.S. Obaidat, G.I. Papadimitriou, A.S. Pomportsis, John Wiley,2003.
|
Wireless transmission has found widespread use in communication system only in the last 15-20 years.
|
|
The popularity of wireless communication systems is due to advantages compared to wireline systems.
|
|
The most important if these advantages mobility and cost savings.
|
|
Wireless networks are also useful in reducing networking costs in several cases.
|
|
The fact can be extremely useful:
|
|
Network deployment in difficult to wire areas,such is the case for cable placement in rivers, oceans, etc.
|
|
Prohibition of cable deployment. This is the situation in network deployment in several cases, such as historical buildings.
|
|
Deployment of a temporary network. In this case, cable deployment does not make sense.
|
|
Deployment of a wireless solution, such as a WLAN is an extremely cost-efficient solution for the scenarios described above.
|
|
1.1 Evolution of Wireless Network
|
|
It is more logical to assume that the origin of wireless networks , as we understand them today , starts with the first radio transmission.
|
|
The origins of radio-based telephony date back to 1915, when the first radio-based conversation was established between ships
|
|
1.1.1 Early Mobile Telephony
|
|
In 1946, the first public mobile telephone system, known as Mobile Telephone System(MTS), was introduced in 25 cities in the US.
|
|
MTS was an analog system, meaning that it processed voice information as a continuous waveform.
|
|
The system was half-duplex, meaning that at a specific time the user could either speak or listen.
|
|
MTS utilized a Base Station(BS) with a single high-power transmitter that covered the entire operating area of the system
|
|
However, since these BSs utilized he same frequencies, they needed to be sufficiently apart form one another so as not to cause interference to each other
|
|
Major limitations of MTS were the manual switching of calls and the fact that a very limited number of channels was available
|
|
1.1.2 Analog Cellular Telephony
|
|
MTS used the spectrum inefficiently, thus providing a small capacity.
|
|
The fact that the large power of BS transmitters caused interference to adjacent systems plus the problem of limited capacity quickly made the system impractical.
|
|
A solution to this problem was found through the use of the cellular concept, which would bring about a revolution in the area of mobile telephony a few decades later.
|
|
Originally proposed in 1947, the cellular concept replaces high-coverage BSs with a number of low-coverage stations.
|
|
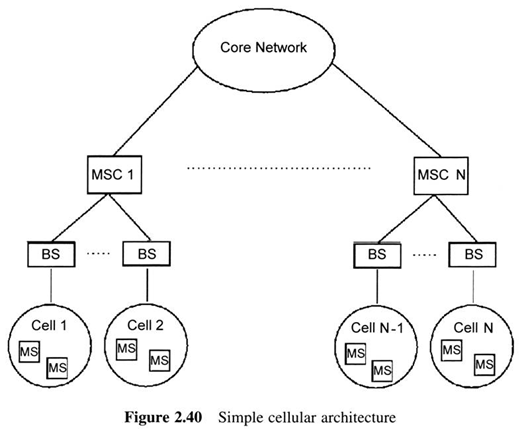
The area of coverage of each such BS is called a ‘cell’.
|
|
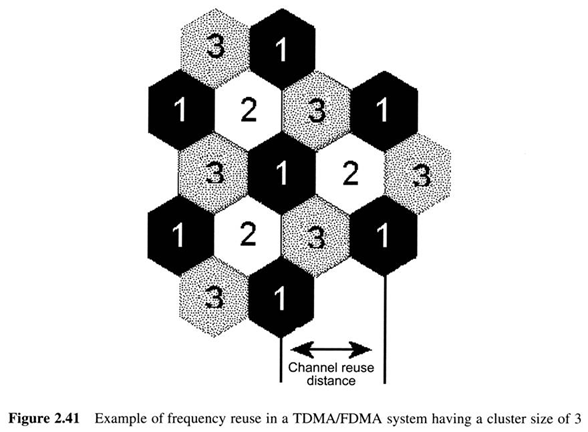
The available spectrum is partition into channels and each cell uses its own set of channels.
|
|
This concept is known as frequency reuse and allows a certain channel to be used in more than one cell, thus increasing the efficiency of spectrum use.
|
|
Each BS is connected via wires to a device known as the Mobile Switching Center(MSC).
|
|
The first generation of cellular systems (1G system) was designed in the late 1960s can be thought as descendants of MTS since they were of also analog systems.
|
|
The first commercial analog system in the Us, known as Advanced Mobile Phone System(AMPS),offer only voice transmission.
|
|
1.1.3 Digital Cellular Telephony
|
|
Analog cellular systems were the first step for the mobile telephony industry.
|
|
Despite their significant success, they had a number of disadvantages were alleviated by the second generation of cellular systems(2G system), which represent data digitally.
|
|
This is done by passing voice signals through an Analog to Digital (A/D) converter and using the resulting bitstream to modulate an RF carrier.
|
|
Compared to analog system, digital systems have a number of advantages :
|
|
Digitized traffic can easily be encrypted in order to provide privacy and security
|
|
Analog data representation made 1G systems susceptible to interference, a highly variable quality of voice calls. In digital systems, it is possible to apply error detection and correction techniques to the voice bitstream.
|
|
In analog system, each RF carrier is dedicated to a user, regardless of whether the user is active or not. In digital systems, each RF carrier is shared by more than one user.
|
|
1.1.3.1 GSM
|
|
Throughout Europe, a new part of the spectrum in the area around 900MHz has been made available for 2G systems.
|
|
Its name was ‘Global System for Mobile Communication’.
|
|
Nowadays, it is the most popular 2G technology, this popularity is not only due to its performance, but also due to the fact that it is the only 2G standard in Europe.
|
|
1.1.3.2 HSCSD and GPRS
|
|
Another advantage of GSM is its support for several extension technologies that achieve higher rates for data applications.
|
|
Two such technologies are High Speed Circuit Switched Data(HSCSD) and General Packet Radio Service(GPRS).
|
|
Contrary to GSM, it gives more than one time slot per frame to a user, hence the increased data rates.
|
|
GPRS operation is based on the same principle as that of HSCSD : allocation of more slots within a frame. However, the difference is that GPRS is packet-switched, whereas GSM and HSCSD are circuit-switched.
|
|
1.1.3.3 IS-95
|
|
In 1993, IS-95, another 2G system also known as cdma one, was standardized.
|
|
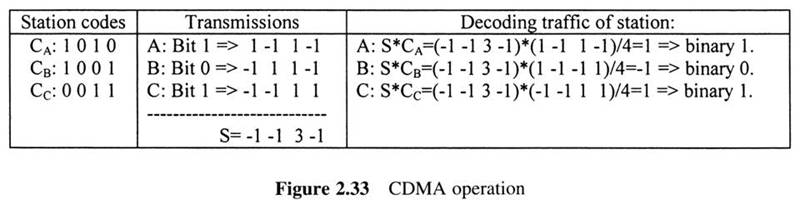
Is-95 utilizes Code Division Multiple Access (CDMA).
|
|
In IS-95, multiple mobiles in a cell whose signals are distinguished by spreading them with different codes, simultaneously use a frequency channel.Thus, neighboring cells can use the same frequencies.
|
|
1.1.4 Cordless Phones
|
|
Cordless telephones first appeared in the 1970s and since then have experienced a significant growth.
|
|
They were originally designed to provide mobility within small coverage areas, such as homes.
|
|
Cordless telephones comprise a portable handset, which communicates with a BS connected to the Public Switched Telephone Network(PSTN).
|
|
The evolution of digital cordless phones led to the DECT system. This is a European cordless phone standard that provides support for mobility.
|
|
A standard similar to DECT is being used in Japan. This is known as the Personal Handy-phone System(PHS). It also supports handoff between BSs.
|
|
1.1.5 Wireless Data System
|
|
Wireless data systems are used for transmission of data.
|
|
These systems are characterized by bursty transmissions : unless there is a packet to transmit, terminals remain idle.
|
|
1.1.5.1 Wide Area Data Systems
|
|
These systems offer low speeds for support of services such as messaging, e-mail and paging.
|
|
Paging systems. These are one-way cell-based systems that offer very low-rate data transmission towards the mobile user.
|
|
Paging systems work by broadcasting the page message from many BSs both terrestrial and satellite. Terrestrial systems typically cover small areas whereas satellites provide nationwide coverage.
|
|
Mobitex.
|
|
This is a packet-switched system developed by Ericsson for telemetry applications.
|
|
Ardis.
|
|
This circuit-switched system was developed by Motorola and IBM.
|
|
Multicellular Data Network(MCDN).
|
|
MCDN was designed for Internet access and thus offers significantly higher speeds than above systems
|
|
1.1.5.2 Wireless Local Area Networks(WLANS)
|
|
WLANs are used to provide high-speed data within a relatively small region, such as a small building.
|
|
The first attempt to define a standard was made in the late 1980s by IEEE Working Group 802.4.
|
|
As a result, the Executive Committee of IEEE Project 802 decided to establish Working Group IEEE 802.11.
|
|
The first 802.11 standard offered data rates up to 2 Mbps using either spread spectrum transmission in the ISM bands or infrared transmission.
|
|
In 1999, two supplements to the original standard were approved by the IEEE Standards Board.
|
|
The first standard, 802.11b, extends the performance of existing 2.4GHz physical layer, with potential data rates up to 11Mbps.
|
|
The second standard, 802.11a aims to provide a new , higher data rate (from 20 to 54 Mbps) physical layer in the 5 GHz ISM band.
|
|
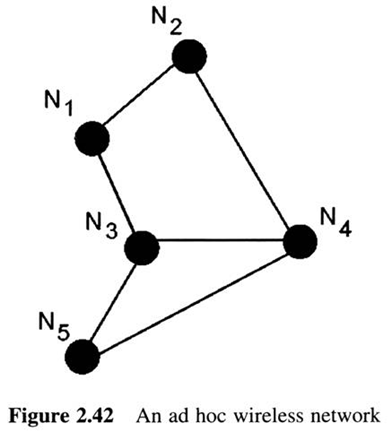
IEEE 802.11 is often referred to as wireless Ethernet and can operate either in an ad hoc or in a centralized mode.
|
|
An ad hoc WLAN is a peer-to-peer network that is set up in order to serve a temporary need.
|
|
1.1.5.3 Wireless ATM(WATM)
|
|
WATM aims to combine the advantages of freedom of movement of wireless networks with the statistical multiplexing and QoS guarantees supported by traditional ATM networks.
|
|
1.1.5.4 Personal Area Networks(PANs)
|
|
PANs are the next step down from LANs and target applications that demand very short-range communications.
|
|
The first attempt to define a standard for PANs dates back to an Ericsson project in 1994, which aimed to find a solution for wireless communication between mobile phone and related accessories.
|
|
This project was named Bluetooth.
|
|
1.1.6 Fixed Wireless Links
|
|
Contrary to the wireless systems presented so far, fixed wireless system lack the capability of mobility.
|
|
Such systems are typically used to provide high speeds in the local loop, also known as the last mile.
|
|
Fixed wireless systems are either point-to-point or point-to-multipoint systems.
|
|
Point-to-multipoint is the most popular form of providing fixed wireless connectivity, since many users can connect to the same antenna transceiver. :
|
|
The most common fixed wireless system are presented below and are typically used for high-speed Internet access :
|
|
ISM-band systems.
|
|
MMDS. (Multipoint Multichannel Distribution System)
|
|
LMDS. (Local Multipoint Distribution System)
|
|
1.1.7 Satellite Communication Systems
|
|
The first real communication satellite was the AT&T Telsart1, which was launched by NASA in 1962.
|
|
From the Telstar era to today, satellite communications have enjoyed an enormous growth offering services such as data, paging, voice, TV broadcasting, Internet access and a number of mobile services.
|
|
1.1.8 Third Generation Cellular Systems and Beyond
|
|
Despite their great success and market acceptance, 2G systems are limited in terms of maximum data rate.
|
|
In order to provide for efficient support of such services, work on the Third Generation(3G) of cellular systems was initiated by the International Telecommunication Union (ITU) in 1992.
|
|
The outcome of the standardization effort, called International Mobile Telecommunication 2000(IMT-2000), comprises a number of different 3G standard.
|
|
These standards are as follows :
|
|
EDGE, a TDMA-based system
|
|
Cdma2000, a fully backwards-compatible descendant of IS-95
|
|
WCDMA, a CDMA-based system
|
|
As far as the future of wireless networks is concerned, it is envisioned that evolution will be toward an integrated system, which will produce a common packet-switched platform for wireless systems, this is the aim of the Fourth Generation (4G) of cellular networks.
|
|
1.2 Challenges
|
|
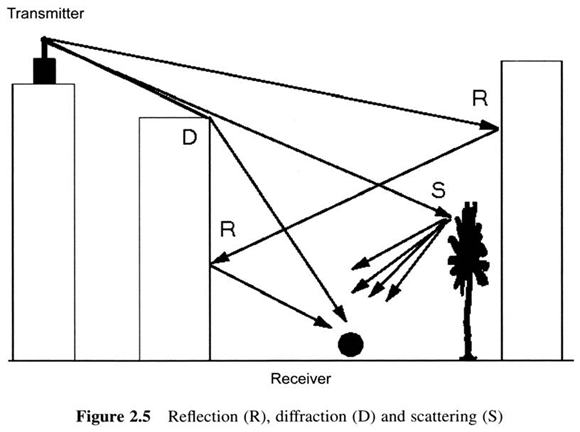
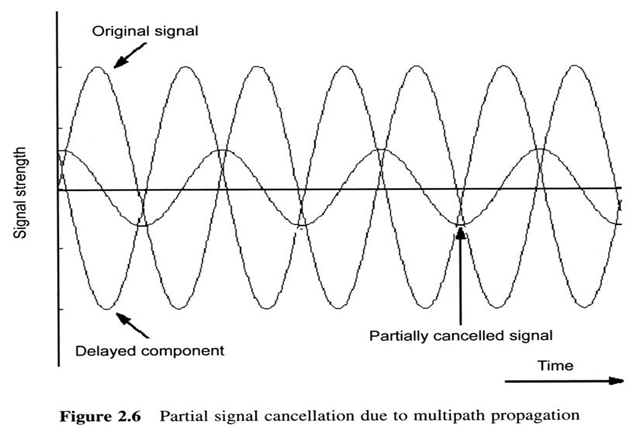
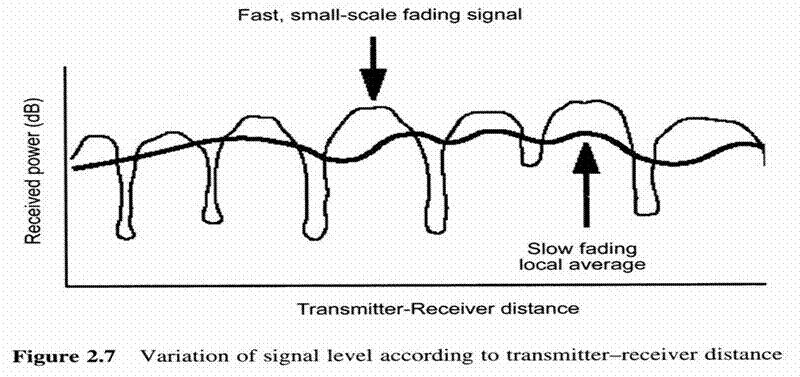
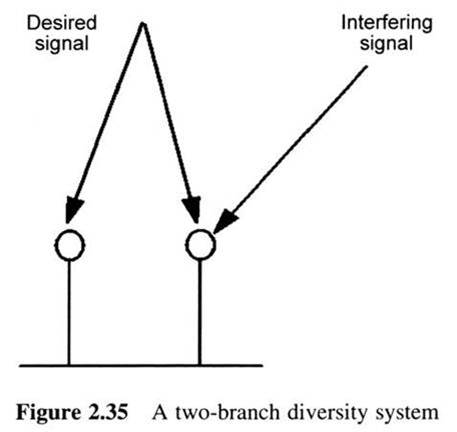
Wireless medium unreliablity
|
|
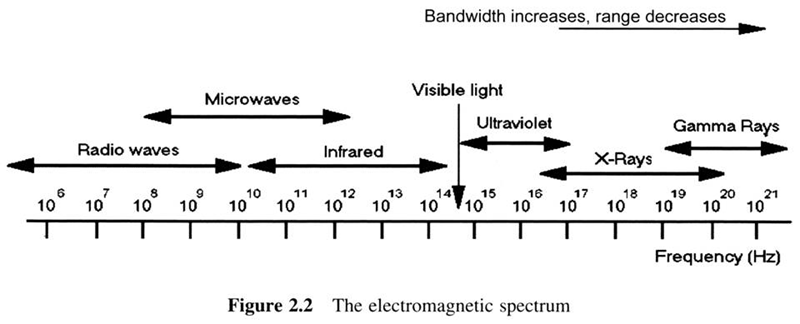
Spectrum use
|
|
Power management
|
|
Security
|
|
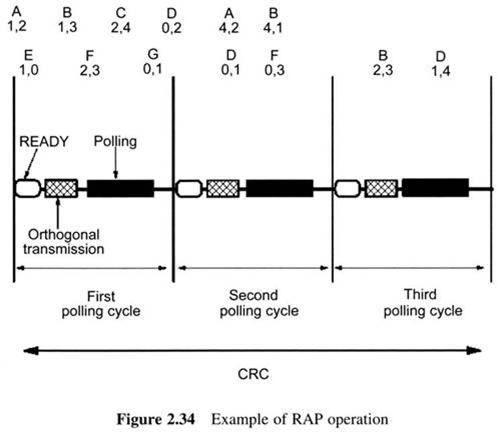
Location/Routing
|
|
Interfacing with Wired networks
|
|
Health concerns
|
BackToTop
Wed Mar 16 00:33:52 CST 2011
Due to the fact that pairs of uplink/downlink channels are allocated by regulation agencies, most of the time they are of the same bandwidth
BackToTop
Wed Mar 16 00:33:54 CST 2011
BackToTop
Wed Mar 16 00:33:56 CST 2011
BackToTop
Wed Mar 16 00:33:57 CST 2011
BackToTop
Wed Mar 16 00:33:59 CST 2011
BackToTop
Wed Mar 16 00:34:00 CST 2011
BackToTop
Wed Mar 16 00:34:03 CST 2011
BackToTop
Wed Mar 16 00:34:04 CST 2011
BackToTop
Wed Mar 16 00:34:06 CST 2011
Principles and Fundamentals



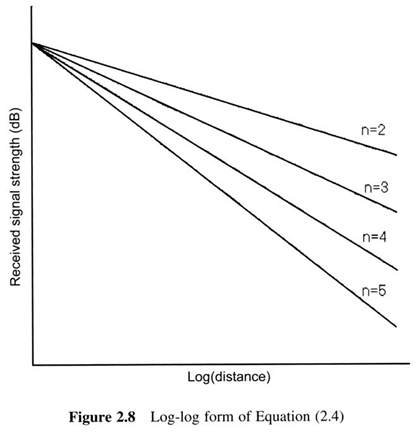
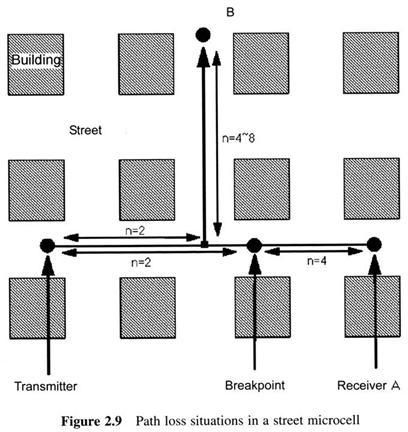
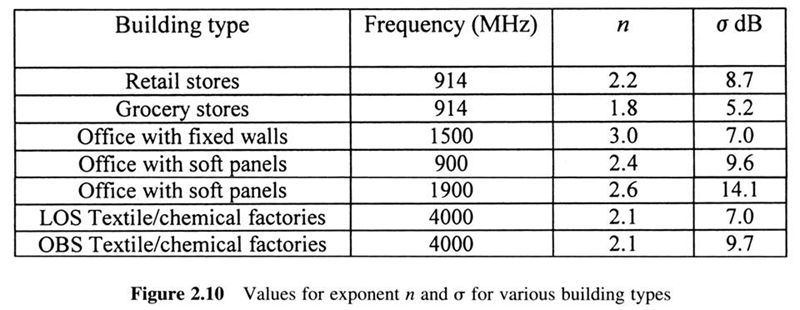
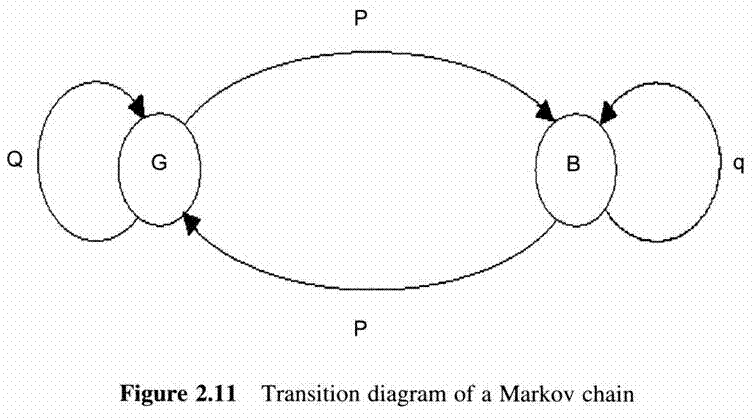
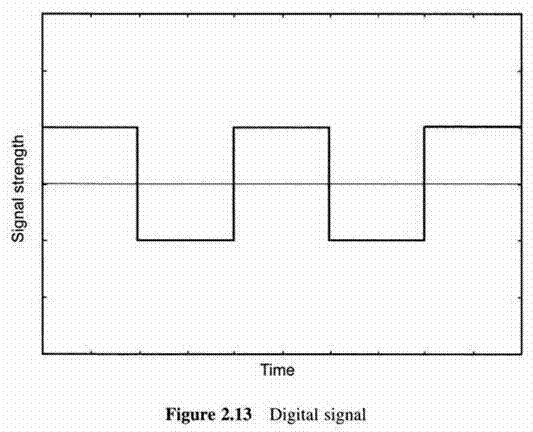
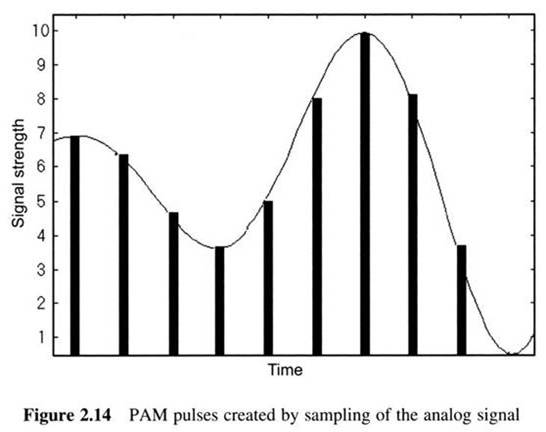
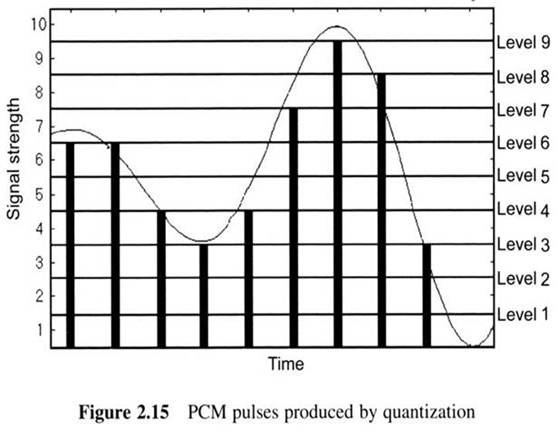
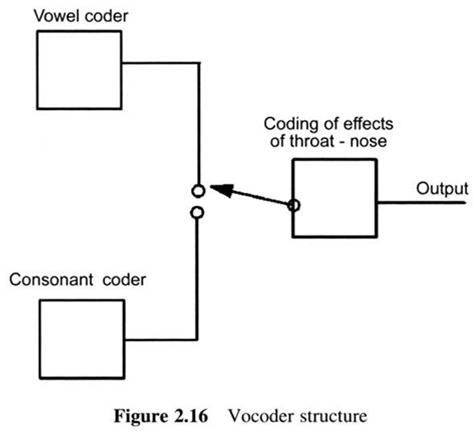
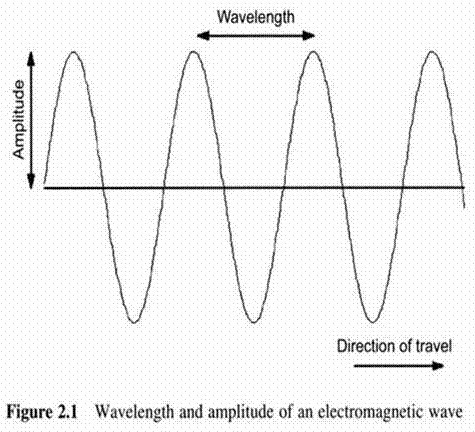
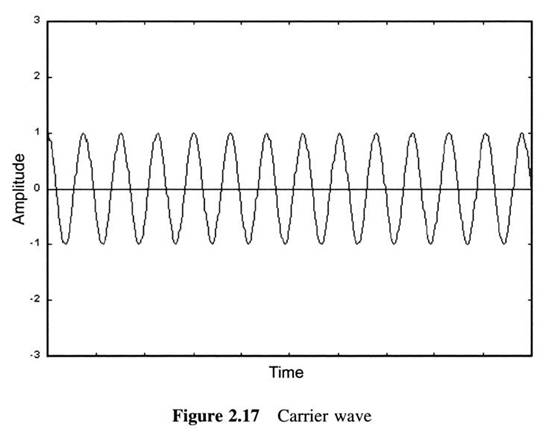
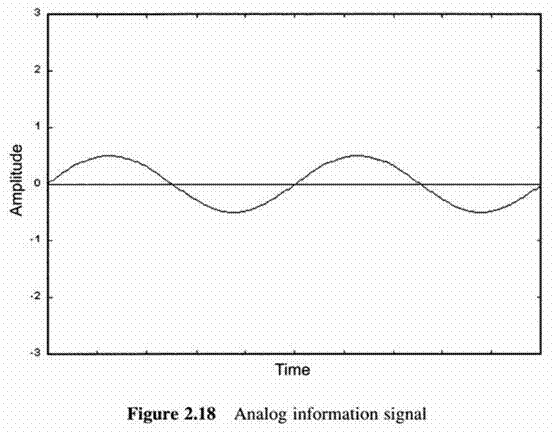
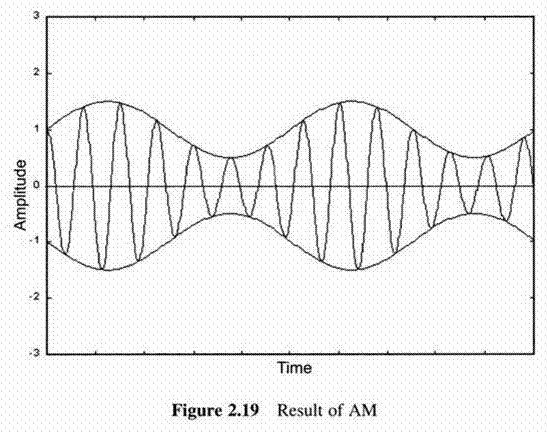
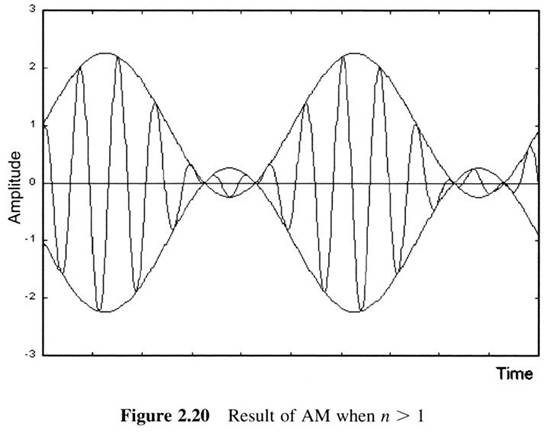
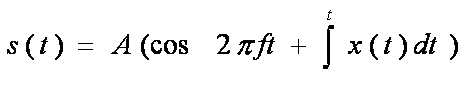
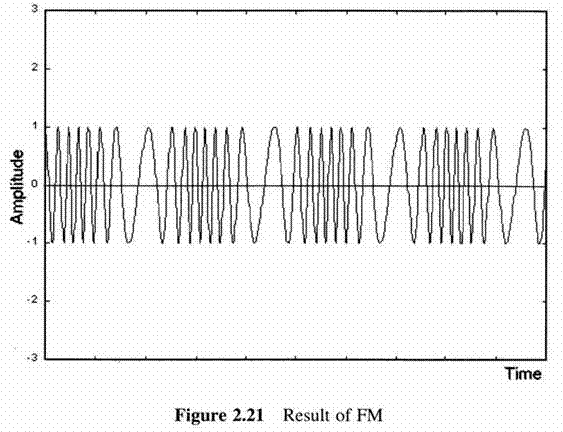
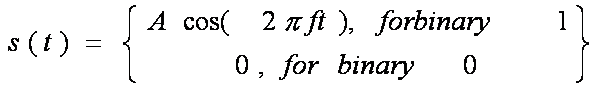

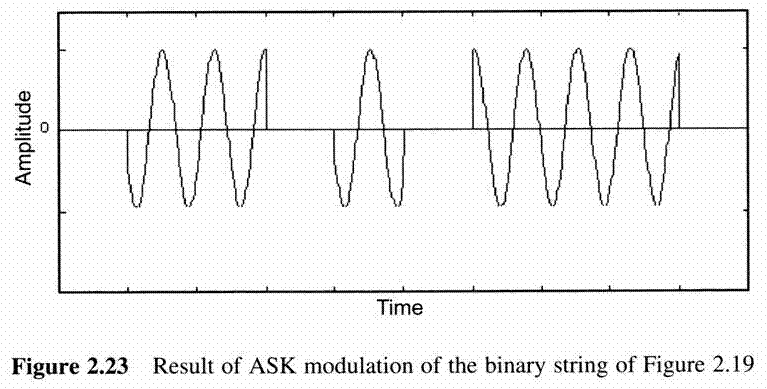
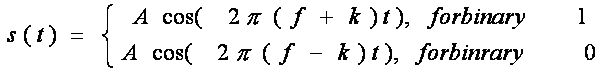
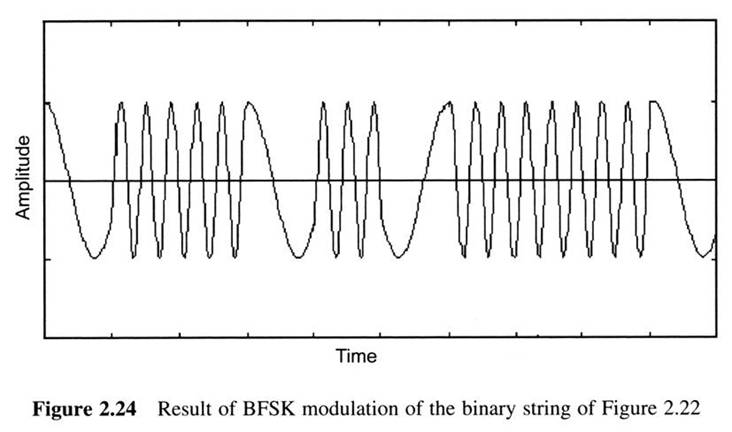
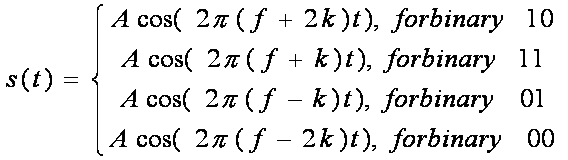
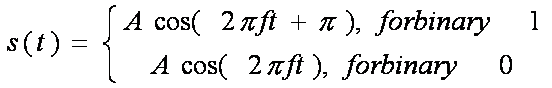
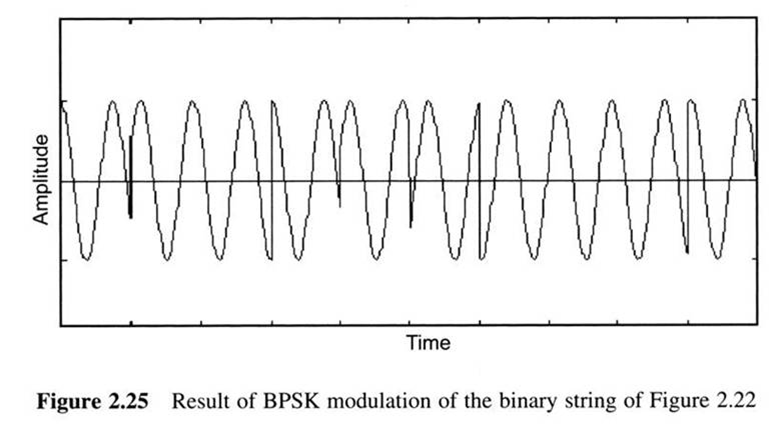
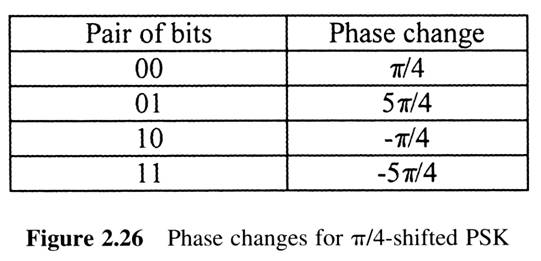
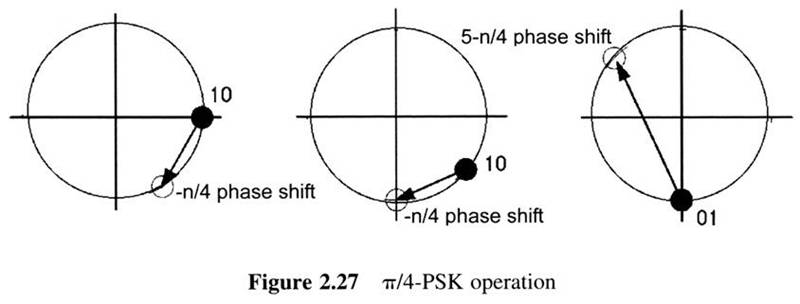
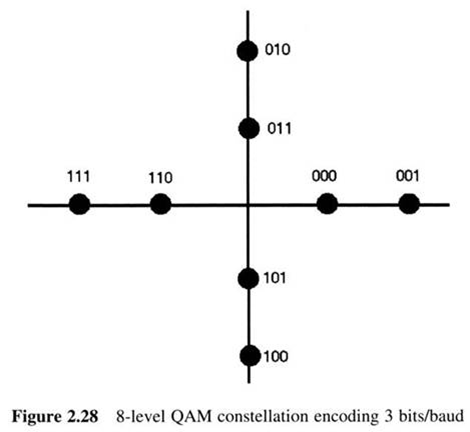
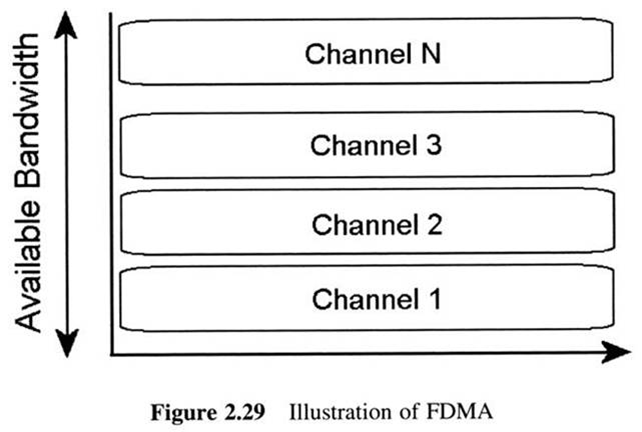

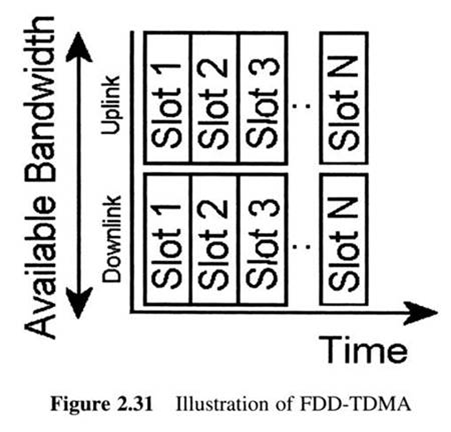
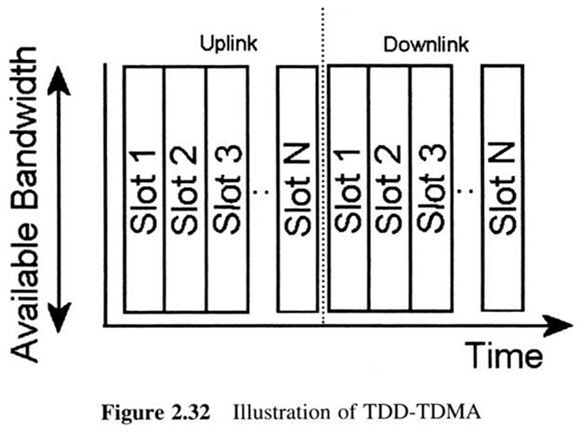
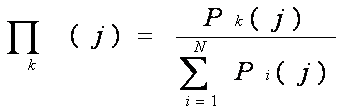
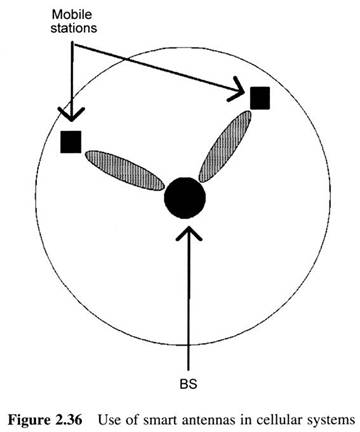
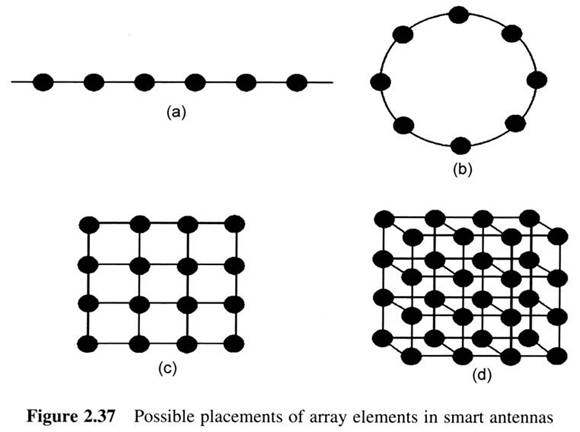
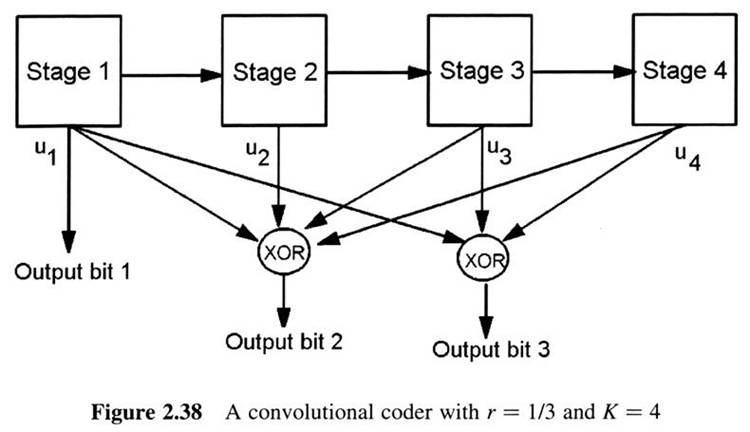
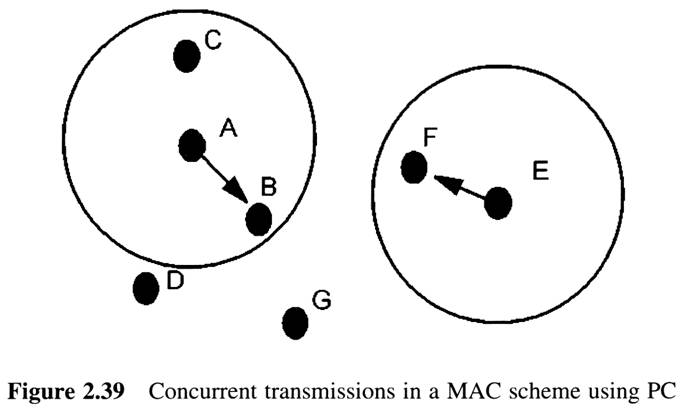

First Generation Cellular Systems
Second Generation Cellular Systems














Third Generation Cellular Systems












XXXXXX


2PDCP Functions

Fixed Wireless Access Systems





Wireless ATM and Ad Hoc Routing











Personal Area Networks (PANs)










Economics of Wireless Networks





